What you need to know about the Meltdown and Spectre CPU exploits
The impact could be more far-reaching than any previous exploit.

2018 is starting off to be a bad year for AMD, ARM, and Intel—mostly Intel. Researchers revealed earlier this week that all CPUs made in the last two decades are vulnerable to hardware-based exploits that aren’t easy to fix, especially without significant performance penalties. Initially, there was just one exploit, based on Intel’s CPU architecture and the ability to execute instructions in a speculative manner, that is, essentially out of order. This helps modern CPUs in significant ways, and is a fundamental part of CPU design.
Unfortunately, two primary attacks based on these fundamental CPU design principles have come to light, one significantly more serious than the other: Meltdown and Spectre. Here’s what you need to know about each.
What are Meltdown and Spectre?
Fundamentally, both exploits use somewhat similar core concepts. All modern processors use various features and techniques, including out-of-order execution (OOOE), branch prediction, and speculative execution to improve performance. However, all of these have the potential to execute code that shouldn't be allowed. The hardware guarantees that the final result will be correct, flushing any results from code that shouldn't have run. The problem is that there are side effects of the OOOE and speculative execution, where they can cause changes to the cache state, and then cache attacks can be used to try and pull 'secrets' (data from RAM) out of the cache.

What is Meltdown?
Meltdown is an exploit that affects Intel CPUs at least since 2011, which leverages elements of out-of-order execution to cause a change in the cache state of a CPU, and then use that to dump contents of memory that should normally be inaccessible. It may affect many other CPUs as well, basically anything that uses OOOE, which includes all Intel CPUs back to the original Pentium Pro (excluding Itanium and Atom before 2013), and AMD CPUs from a similar time period. While the current full implementation of Meltdown does not work on AMD and ARM CPUs, there are indications that further modification of the code could allow a similar attack to work on AMD and ARM processors. The KPTI (and similar) patches that have been deployed for Windows, OS X, and Linux largely mitigate the problem, though there are still some less critical remaining concerns.
It's important to note that many of these exploits aren't actually new. From the whitepaper, "The fact that hardware optimizations can change the state of microarchitectural elements, and thereby imperil secure software implementations, is known since more than 20 years. Both industry and the scientific community so far accepted this as a necessary evil for efficient computing." What has changed is that Meltdown is a working attack vector on many Intel CPUs. The good news is that all the major operating systems should already be patched to mitigate problems.
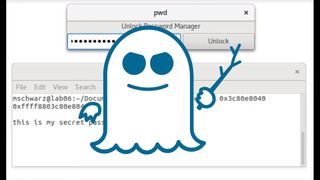
What is Spectre?
Spectre uses a processor's speculative execution capability and branch prediction, combined with similar approaches to those in Meltdown (eg, cache attacks like Evict+Time), to read secrets from a process's memory. The attack involves training a branch predictor to take one path, and then after many iterations, using a branch mispredict to cause speculative execution of code that shouldn't be run. Up to nearly 200 instructions could be run in some instances. Spectre can affect processors from AMD, ARM, Intel, and others—any processor that uses branch prediction, in theory, which is basically every modern processor—but the attack must be tailored somewhat specifically to the hardware, making it more difficult to implement.
Protecting against Spectre is also more difficult. As the whitepaper puts it, "More broadly, there are trade-offs between security and performance. The vulnerabilities in this paper, as well as many others, arise from a longstanding focus in the technology industry on maximizing performance. As a result, processors, compilers, device drivers, operating systems, and numerous other critical components have evolved compounding layers of complex optimizations that introduce security risks. As the costs of insecurity rise, these design choices need to be revisited, and in many cases alternate implementations optimized for security will be required."
In other words, making our processors faster has come at the cost of security, and the only real fix may end up being to slow things down.
When Intel says "this isn't a bug" what it really means is "please don't make us recall millions of faulty processors" pic.twitter.com/NPU3WSEjSIJanuary 4, 2018
Will Meltdown and Spectre impact my home PC?
Directly, both Meltdown and Spectre won’t really impact your PC any more than a random virus. There are thousands of viruses circulating at any given time, and if you already practice safe computing, you shouldn't be impacted by anything trying to leverage the Meltdown and Spectre vulnerabilities. If you get a virus on your home PC, it's already compromised, and Meltdown and Spectre don't really make the risk any worse.
The main concern revolves around the fix, which is reported to cause a significant slowdown in specific high I/O tasks. Games are generally more GPU bound than they are CPU bound and do not make many or any direct kernel calls at all, so even if the fix impacts you, the performance degradation will likely be small and unnoticeable. Initial benchmarks using Linux and Windows indicate very little change (less than three percent) in performance for common tasks, with data compression (eg, 7-zip) being one of the hardest hit. Gaming benchmarks saw no difference.
The greater risk is for anyone using cloud services. Meltdown as an example is able to read all memory contents on a system from a virtual machine (VM), without breaking any of the security protocols. But unless you’re running a server farm at home, with tenants that might try stealing data from other tenants, you should be fine.
Does Meltdown and Spectre affect gaming services?
Any company that fully controls its hardware should be relatively safe from attack. So if all of Steam's servers, as an example, are only running Steam VMs, there's little risk. The same goes for any other provider. The main concern is with services that rent or lease time on servers that may be running processes from other companies.
Which companies are at most risk from Meltdown and Spectre?
Any company providing or using cloud hosting services should be patched against these attacks as soon as possible. That includes large providers like Amazon AWS, Google Cloud Platform, Microsoft Azure, and many others. Any server that runs VMs from multiple users could have data leak from one VM to another, if it's not patched. This is particularly problematic for smaller hosting services that run sometimes hundreds of smaller websites via containers, and the fixes could be very costly for such providers.
You may have heard about @Intel's horrific #Meltdown bug. But have you watched it in action? When your computer asks you to apply updates this month, don't click "not now." (via https://t.co/J84n79LRIA & @misc0110) pic.twitter.com/cWEiZWZdcJJanuary 4, 2018
What can I do?
The primary worry should be with websites and services that you use—how secure are they, and have they put measures into place to protect your data? The answer to those questions may not always be immediately available, unfortunately. For home PCs and laptops, you should update with the latest security patches to Windows, macOS, and Linux. For most of our readers, Windows is the primary OS, and patches are available for Windows 10, Windows 8.1, and Windows 7.
Windows 10 users should check for update KB4056892 and install it. However, official government advisors indicate that updating the operating system isn't enough, and that low-level firmware (BIOS and CPU microcode) is required.
Intel has worked with partners on both software patches and firmware updates for most of its recent processors, though in the case of firmware it will be up to the system vendor or motherboard manufacturer to pass along the necessary fix. Intel states that the updates "render those systems immune from both exploits [Meltdown and Spectre]," though the fixes are only for most processors made within the past five years. If you have an older system, you may be left vulnerable.

Do Meltdown and Spectre affect AMD CPUs?
AMD claims that its CPU architecture is immune to the attacks, though this statement may have been made prematurely. Because exploits have different variants, current analyses only show that AMD CPUs are safe against the current version of Meltdown, which focuses primarily on Intel’s architecture. The Meltdown paper has the following statement:
"We also tried to reproduce the Meltdown bug on several ARM and AMD CPUs. However, we did not manage to successfully leak kernel memory with the attack described in Section 5, neither on ARM nor on AMD. The reasons for this can be manifold. First of all, our implementation might simply be too slow and a more optimized version might succeed. For instance, a more shallow out-of-order execution pipeline could tip the race condition towards against the data leakage. Similarly, if the processor lacks certain features, e.g., no re-order buffer, our current implementation might not be able to leak data. However, for both ARM and AMD, the toy example as described in Section 3 works reliably, indicating that out-of-order execution generally occurs and instructions past illegal memory accesses are also performed."
So far, then, AMD processors haven't been affected by Meltdown, but they're not immune against Spectre, which uses a wider range of speculative execution features. Spectre impacts CPUs from AMD, ARM, and Intel, and the cure may in some ways be worse than the disease, depending on how much it impairs performance.
Does having an anti-virus help protect me against Meltdown and Spectre?
Yes and no. Anti-virus vendors are updating their products to look out for viruses that utilize Meltdown and Spectre exploits. So if you have an anti-virus—Windows's built in Windows Defender counts—that is updated, you can feel a little easier knowing that your PC is safer, for now.
However, an anti-virus is just local protection. Meltdown and Spectre does the most damage to large scale company's that provide services that you might use every day: banks, streaming services, e-commerce, gaming, etc. If that sounds like everything to you, it is. Microsoft, Google, Amazon and others are rushing to implement fixes for Meltdown, but Spectre is going to take a bit more analysis.
The best thing to do right now is make sure Windows is updated. Google also stated that it would release a new version of Chrome on January 23 that blocks against Meltdown. Intel is working on patching its CPU lineup through microcode updates that you will probably see from your motherboard vendor.
Looking forward
This is clearly not the last we've heard of this sort of attack or exploit, and if anything, we've learned not to speculate about what may happen in the future. It's worth pointing out that some of the techniques used in both Meltdown and Spectre (eg, side-channel cache attacks) are not really new, and the performance benefits have often outweighed the potential security risks. Unfortunately, burying our heads in the sand and hoping no one will do anything bad with security vulnerabilities isn't an acceptable approach, and with the cats out of the bag you will want to be extra vigilant in regards to passwords and other sensitive information.
The biggest gaming news, reviews and hardware deals
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
Jarred's love of computers dates back to the dark ages when his dad brought home a DOS 2.3 PC and he left his C-64 behind. He eventually built his first custom PC in 1990 with a 286 12MHz, only to discover it was already woefully outdated when Wing Commander was released a few months later. He holds a BS in Computer Science from Brigham Young University and has been working as a tech journalist since 2004, writing for AnandTech, Maximum PC, and PC Gamer. From the first S3 Virge '3D decelerators' to today's GPUs, Jarred keeps up with all the latest graphics trends and is the one to ask about game performance.