Google sums up 2023's security exploits: the good news is fixes are blocking some types of zero-day attack. The bad news is Windows has seen more than most
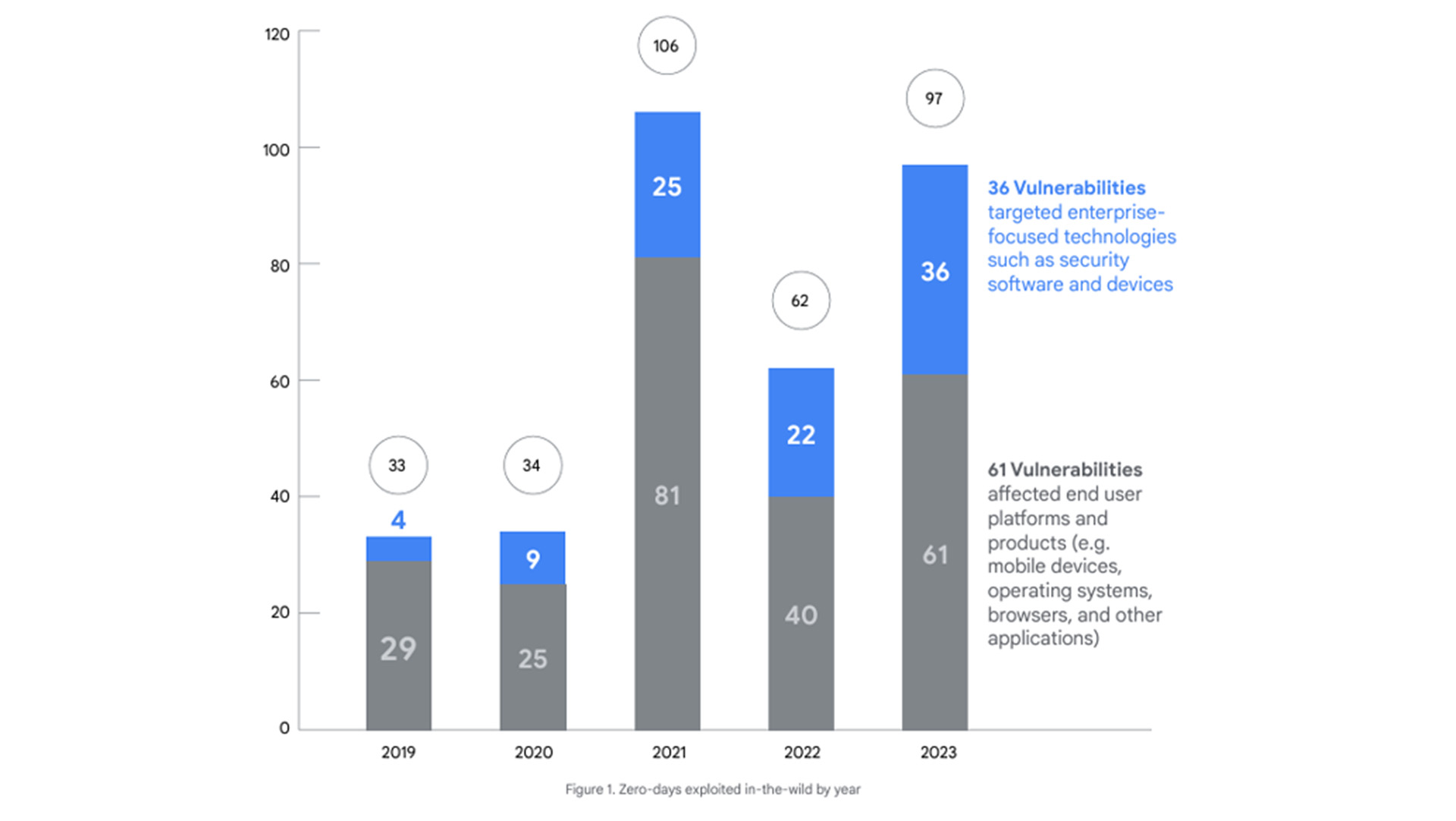
2023 also saw a greater number of zero-day attacks in the wild than 2022, but still fewer than 2021.

2023 was a bumper year for zero-day exploits—50% more zero-day vulnerabilities were exploited last year compared to 2022—and the majority of them affected operating systems and products used by run-of-the-mill end users, such as Windows, Chrome and iOS. Though before the doom and gloom sinks in, Google does have some positive things to say about software security in 2023 in its yearly threat report.
Google's Threat Analysis Group (TAG) and Mandiant keep track of all the zero-day security vulnerabilities they discover out in the wild. Any hole in a security system that some nasty person wearing a long trench coat can take advantage of goes onto their joint yearly report (pdf), separated into whether it impacted end-users or enterprise software.
The first takeaway from the report is that there was a sharp increase in both end-user and enterprise zero-day vulnerabilities in 2023 compared to 2022. It notes 61 exploits impacting end-user software, such as operating systems, and 36 for enterprise software. That's compared to just 40 and 22, respectively, the year before. That might seem bad but end-user software had it a lot worse in 2021 at 81 counts.
The largest share of end-user exploits noted in the report go to Windows at 17, an increase of four on last year. The biggest increase year-on-year was actually for Apple's own brand of browser, Safari, which gained eight new exploits taking it up to 11 overall.
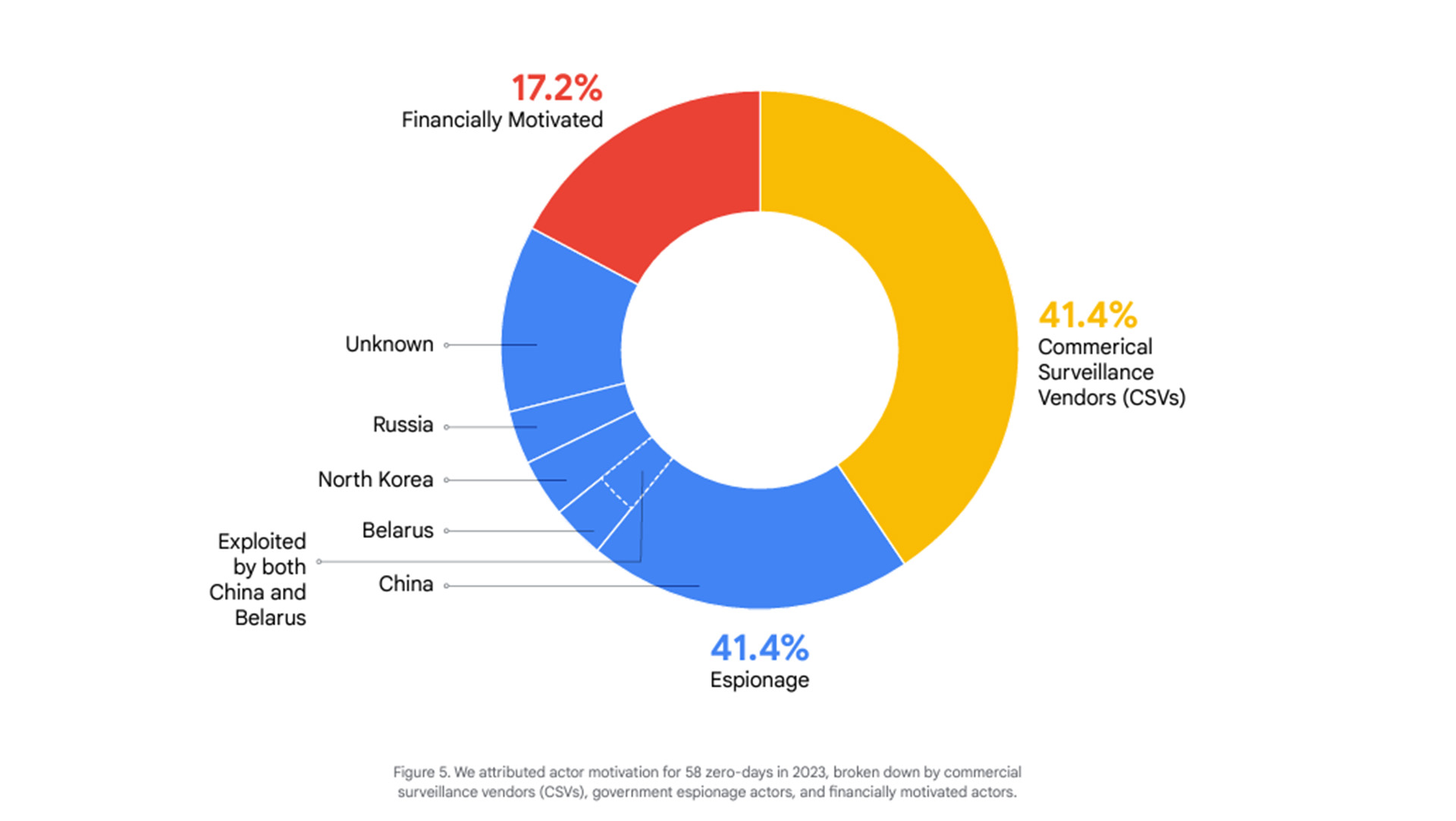
Surprisingly only a few exploits in the report were suspected of being financially motivated. Most were either government-led espionage or done by commercial surveillance vendors (CSVs), spyware firms that actually develop "exploits against end-user products and platforms for use in highly targeted operations by government actors." Must be a fun bunch.
Google's report says the People's Republic of China leads the way in government-backed exploitation: "PRC cyber espionage groups exploited 12 zero-day vulnerabilities in 2023, up from seven in 2022," the report states.
Zero-day attacks can be pretty dangerous. They're by definition attacks that exploit vulnerabilities in software that are not known to the software's creator and thus cannot be stopped. Not all zero-day attacks are discovered by nefarious people with nefarious intentions, however, and some are scooped up ahead of time to be patched before they're exploited 'in the wild'.
The biggest gaming news, reviews and hardware deals
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
The good news is that investments to prevent such exploits are actually seen to be working, namely in reducing the risk of certain classes of vulnerabilities. Speaking to Google's own efforts, the report states that none of the exploits it caught affecting Chrome had anything to do with so-called "use-after-free" exploits that have been prevalent in previous years. This, it claims, is due to the multiple mitigations since released to try and patch the browser up.
The report also praises iOS's Lockdown mode, which helps protect particularly security-sensitive users from bad actors. Likewise, Memory Tagging Extension (MTE) for Arm CPUs is rolling out on some Android phones and Google is pretty hopeful this will have a positive impact, too.
"...it is clear that the steps we as security researchers and product vendors are taking are having an impact on attackers," the report says. "However, we must recognize that our successes will likely manifest as actors increasingly targeting wider and more varied products, as the tried and true methods increasingly become less viable."
"Simply put, more technology offers more opportunity for exploitation."
As for the humble end-user, the best advice I can give is, as ever, make sure to update your software as frequently as you are able. This ensures you're always up to date with the latest mitigations and won't fall foul of some government-sponsored espionage. Or more likely, some bad actor looking to make a quick buck from selling your data.
Best gaming monitor: Pixel-perfect panels.
Best high refresh rate monitor: Screaming quick.
Best 4K monitor for gaming: High-res only.
Best 4K TV for gaming: Big-screen 4K PC gaming.

Jacob earned his first byline writing for his own tech blog. From there, he graduated to professionally breaking things as hardware writer at PCGamesN, and would go on to run the team as hardware editor. He joined PC Gamer's top staff as senior hardware editor before becoming managing editor of the hardware team, and you'll now find him reporting on the latest developments in the technology and gaming industries and testing the newest PC components.


