Narrative hacking RPG Midnight Protocol is now available on Steam

There’s something exciting about a battle of wits in cyberspace; something enchanting about being able to change the world with only a keyboard.
Unfortunately, video game hacking is usually either relegated to a series of progress bars or so complex that it requires a mountain of tutorials. And it rarely has as much of an impact on gameplay as it feels like it should. Developer LuGus studios wanted to change that.
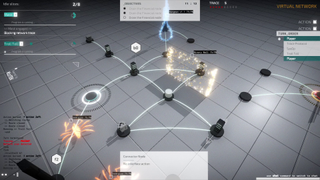
That’s how Midnight Protocol came to be. A narrative-focused strategy RPG set in a not-so-distant future, the title exists in a world where the Internet of Things has progressed to its natural end point. Amidst a backdrop of automation, big data, and machine learning, you’ll step into the shoes of a prominent hacktivist known only as Data.
If you’ve ever wanted to feel like a hacker without having to suffer through hours of tutorials, this is the game for you.
As Data, you’ve made a name for yourself by blowing the whistle on corruption across both the public and private sector. As it turns out, someone didn't appreciate what you'd been doing. In spite of your best efforts, you’ve been doxxed.
They tried to blackmail you. They tried to have you arrested and criminally charged. They failed, and now they're going to find out what that means.
You aren't about to take this lying down. You’ve been doing this for a while, and you’re far from helpless. It’s time to pick yourself up, dust yourself off, and show them what you can do.
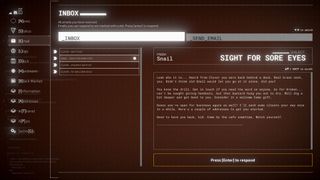
The way you go about that, though, is entirely up to you.
Identity plays a big role in the narrative of Midnight Protocol. Over the course of the game, you have full freedom to decide precisely what kind of hacker you want to be. And as your reputation grows, the story will change in turn.
Will you be a principled, ideological white hat pursuing the greater good? Will you be a ruthless black hat who's just in it for yourself? Or will you blend the disciplines, using whatever tactics you deem necessary as you track down whoever was responsible for doxxing you?
This is not just decided across the main story, either. Over the course of the game, you’ll have access to dozens of sidequests rich with easter eggs for the eagle-eyed science fiction fan. Many of these easter eggs even go so far as to break the fourth wall, requiring you to think like a hacker in the real world — editing your save, for instance, or finding a secret file hidden in the game's folders.
These quests provide hours of additional content, and even more opportunities to define precisely the sort of hacker you want to be.

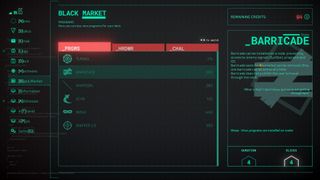
Whatever route you take, you’ll need to be smart about it. Navigating the complex web of connected devices and hardened servers will require both a light touch and careful planning. Luckily, you have a rich arsenal of hacking tools at your disposal, from jackhammers, cloaking software and more—and whenever you need new hardware or software, the black market is readily accessible.
Midnight Protocol takes place entirely within a futuristic hacking interface, controlled entirely via your keyboard. This is your home base, where you’ll do everything from upgrade your deck to initiate hacking operations. Speaking of operations, here’s where Midnight Protocol really shows off its unique flair.
Prior to an operation, you’ll want to customize your deck to fit your unique playstyle.
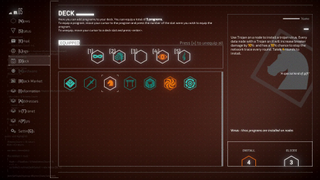
Maybe you’ll overwhelm a network with a distributed denial of service attack before quietly slipping in the back door. Perhaps you’ll pose as a legitimate user, constructing a profile based on carefully-collected data. Or maybe you’ll show up with malware in hand, leaving nothing but binary soup in your wake.
However you decide to approach things,, during a hack you’ll need to manually type in the commands you want to use. That might sound complicated at first glance, but it isn’t. Instead, it adds a layer of immersion as you type commands to access data, evade rival hackers, break through security protocols, and more—no computer science degree required.
They thought you the perfect target for blackmail. They thought doxxing you would be enough for them to be rid of you. They were wrong.
You’re about to show them that. Whoever they are, you’ll find them. You’ll make them answer for what they did.
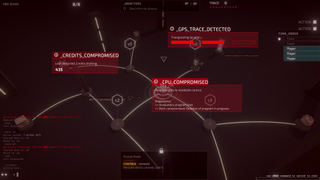
But will you be ready for what you uncover when you do?
Midnight Protocol is available on Windows, Mac OS, and Linux.
PC Gamer Newsletter
Sign up to get the best content of the week, and great gaming deals, as picked by the editors.
