Intel posts benchmarks showing performance impact of new CPU flaws
Once again, storage takes the biggest hit.

After yesterday's revelation that many of Intel's processors dating back to at least 2008 are affected by another series of security flaws somewhat similar to Spectre and Meltdown, you might be wondering what kind of performance impact the upcoming mitigations will have. The answer, according to Intel, maker of some of the best CPUs for gaming, is not much. To show this, Intel posted a small handful of cherry-picked benchmarks.
Before we get to those, give Jarred's write up a read to get up to speed on what's going on, if you have not down so already. Wired digs into the background for even more details, but the short version is that Intel and various security researchers announced the discovery of additional CPU flaws affecting a plethora of CPUs.
Intel collectively refers to these as MDS attacks, or Microarchitecture Data Sampling, and that is the term we will use as well. Part of what's interesting, if not predictable, is that Intel and some security researchers are at odds over how serious this exploits really are, and whether it's necessary to disable Hyper Threading.
Intel contends that's unnecessary, but either way, its message is that the mitigations have a "limited performance impact for the majority of PC clients." According to Intel's own benchmarks, the impact on gaming will be especially negligible, if not nonexistent. Have a look:
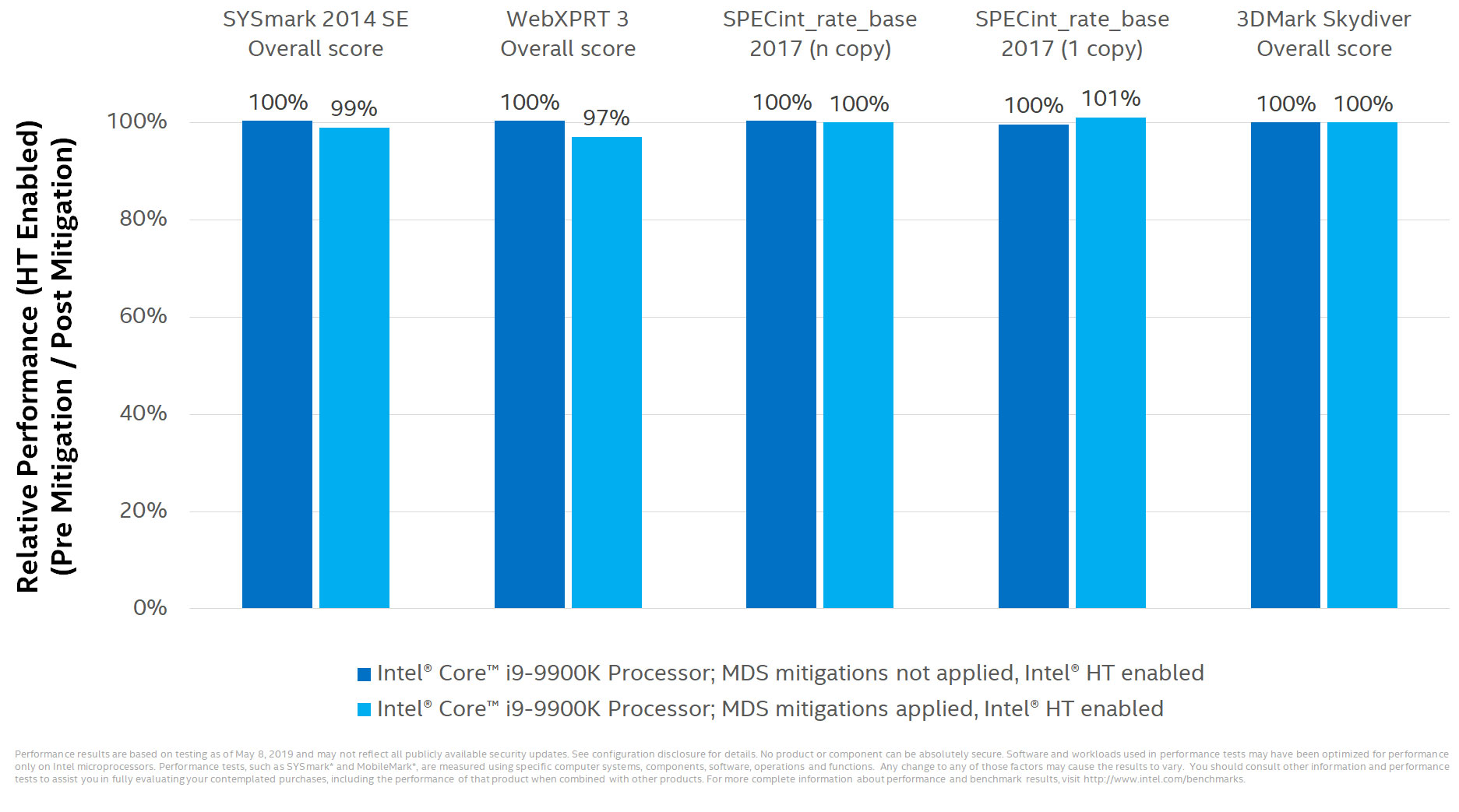
As it pertains to gaming, the only relevant entry is the 3DMark Skydiver score. Intel's testing on a Core i9-9900K shows that performance is the same before and after applying any necessary patches to mitigate the MDS threat, with Hyper Threading enabled.
The other benchmarks show anywhere from a minor performance hit, to even slightly better performance after applying security patches.
Things are a little different if opting to disable Hyper Threading, as some researchers recommend doing. Intel itself even concedes that it may be "appropriate" for some users to take that step, though holds firm on saying it's not recommended in general.
The biggest gaming news, reviews and hardware deals
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
"Once these updates are applied, it may be appropriate for some customers to consider additional steps. This includes customers who cannot guarantee that trusted software is running on their system(s) and are using Simultaneous Multi-Threading (SMT). In these cases, customers should consider how they utilize SMT for their particular workload(s), guidance from their OS and VMM software providers, and the security threat model for their particular environment. Because these factors will vary considerably by customer, Intel is not recommending that Intel HT be disabled, and it’s important to understand that doing so does not alone provide protection against MDS," Intel says.
For those who decide to take the extra precaution, here is how performance shakes out, based on Intel's own testing:
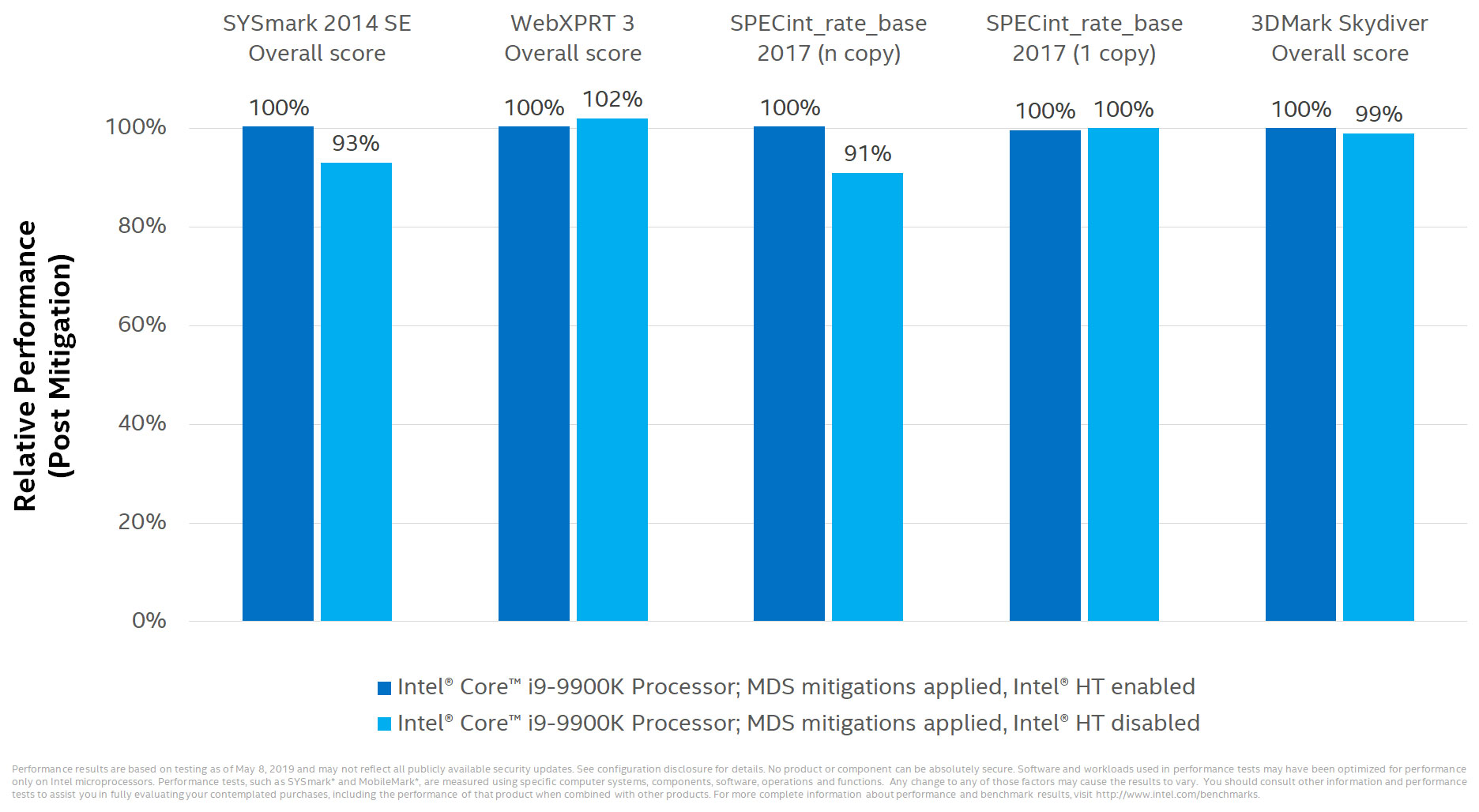
The performance delta widens a bit, though in 3DMark, Intel shows just a 1 percent drop in performance.
It's in workstations and data centers that mitigations are likely to have the biggest performance impact, depending on the workload. In a separate graph, for example, Intel shows a 19 percent drop in "server side Java" performance after disabling Hyper Threading on a Xeon Platinum 8180 processor (compared to having it turned on).
One final note—storage performance took the biggest hit from the Meltdown patches, and it looks like that might be the case with MDS mitigations as well. Have a look:
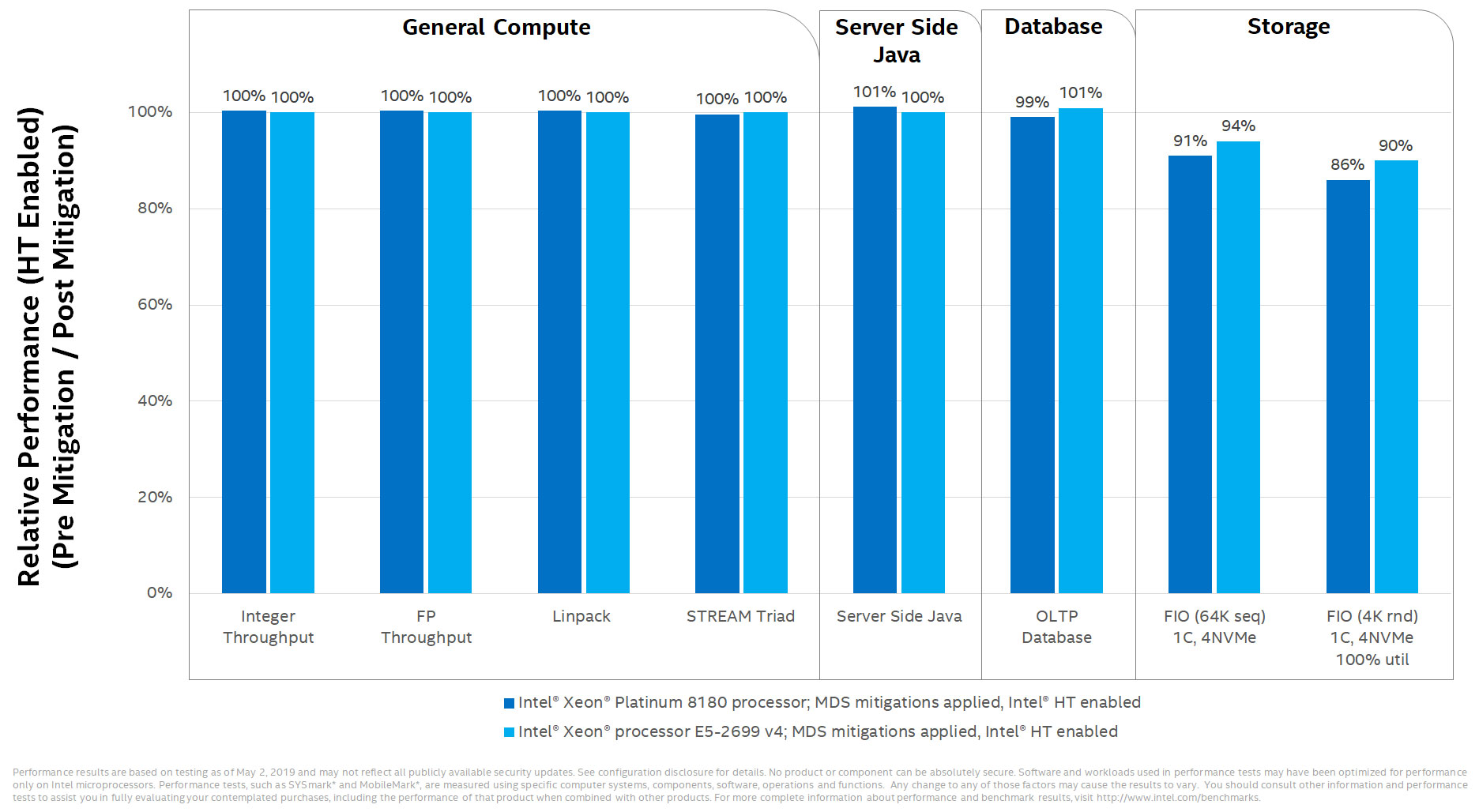
Intel's benchmarks show a 6-14 percent drop in storage performance on a couple of Xeon processors, both with Hyper Threading enabled. Assuming that Intel is not showing a worst case scenario in any of these benchmarks, the hit to storage could be even bigger.
On the bright side, Intel says these new vulnerabilities are addressed in hardware starting with "select 8th and 9th generation" Core processors, and it expects that to be the case with all future CPUs as well. That doesn't mean there won't be other vulnerabilities that show up, but at least for this round, new chips on the horizon will be protected at the hardware level.
For existing CPUs, Intel has put together a guide that shows what mitigations are available (hardware, software, or both) for various CPUs and speculative vulnerabilities, including Spectre, Meltdown, MDS, and others. It's not the most neatly sorted thing in the world, but it's better than nothing. And as a reminder, you can download a tool from this MDS attack site to see if your CPU is affected by the newest threats.
Paul has been playing PC games and raking his knuckles on computer hardware since the Commodore 64. He does not have any tattoos, but thinks it would be cool to get one that reads LOAD"*",8,1. In his off time, he rides motorcycles and wrestles alligators (only one of those is true).


